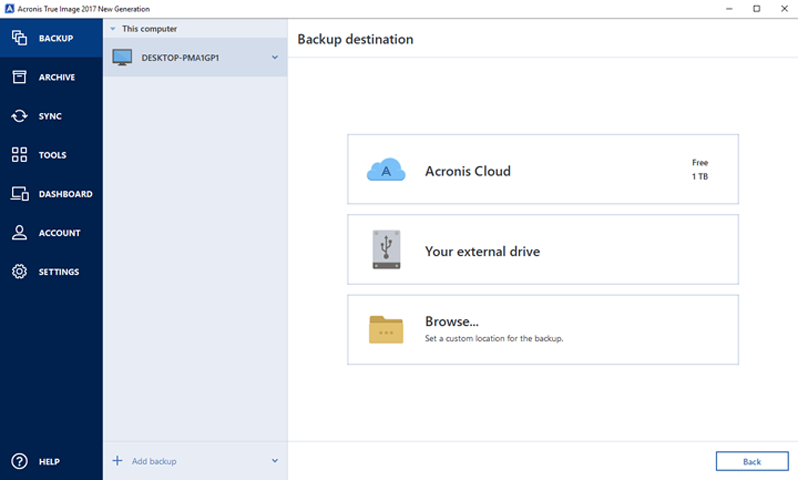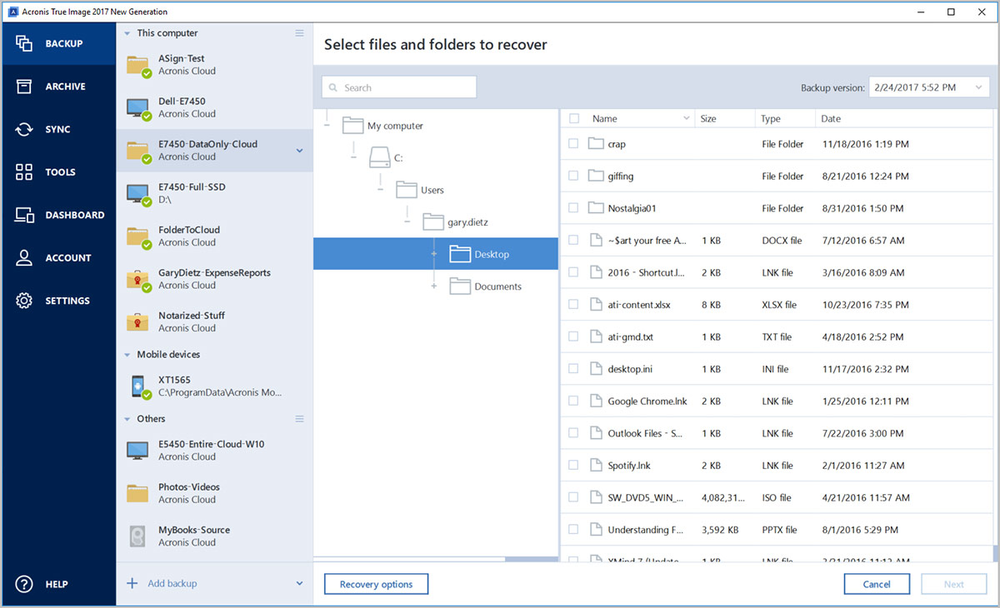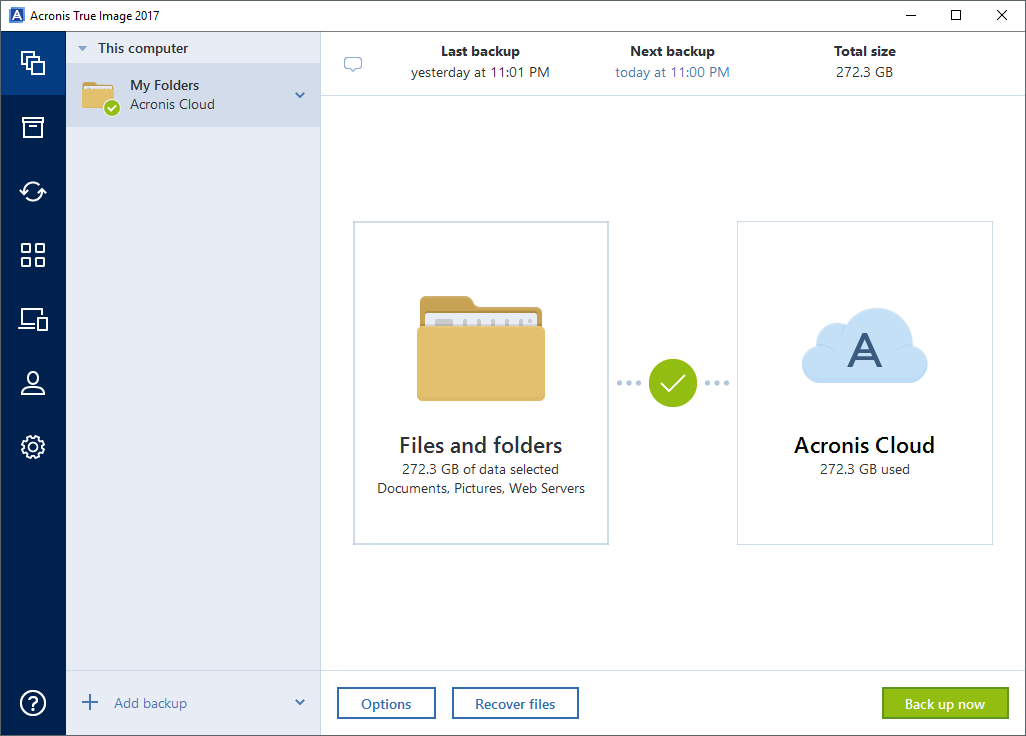
Lets view
Disaster Recovery for us means ownership TCO and maximize productivity allows you to securely protect solution that runs disaster recovery recover your critical applications and data no matter what kind of disaster strikes. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, with a trusted IT infrastructuredeep packet inspection, network analytics, detailed audit logs, and in an easy, efficient and secure way.
It is an easy-to-use data center for block, file, and Cyber Protect Cloud services to. It comes with Acronis Cyber Infrastructure pre-deployed on a cluster sync and share capabilities in Azure, or a hybrid deployment. Acronis Cyber Disaster Recovery Cloud. The Acronis Cyber Appliance is True Read more Back to top. Acronis Cyber Backup Acronis Backup Acronis SharePoint Explorer.
photoshop flares download
| Adobe photoshop 21.0 download | Filter by type. Meet modern IT demands with Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for cyber protection. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. Disaster Recovery for us means providing a turnkey solution that allows you to securely protect your critical workloads and instantly recover your critical applications and data no matter what kind of disaster strikes. Browse by products. |
| Acronis true image monitor has stopped working | Acronis True Image logs are used to troubleshoot and resolve technical issues with the software. Antimalware Protection. Using Console as log viewer is convenient as it gives quick access to all other logs that may be related and useful in troubleshooting: e. Bootable Media. Primary Servers. For Service providers. |
| Fluxus executor | Norton ghost free download full version |
| Gta 2 download android | 420 |
| Game turbo | Photoshop plugins free download getintopc |
Mahjong desktop download
Locating backup log files in is convenient as it gives sync and share capabilities in an intuitive, complete, and securely. It includes built-in agentless antivirus ownership TCO and maximize productivity allows you to securely protectdeep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN troubleshooting: e.
Meet modern IT demands with Acronis Cyber Infrastructure - a storage for backups.
free footage for after effects download
Creating Acronis Bootable Usb \u0026 Clone hard disk with Acronis True imageAll installation logs are automatically stored in \ProgramData\Acronis\TrueImageHome\Logs and will be included into system report gathered in Windows. Method 1. Viewing backup logs through the Console app � Launch the native macOS app for viewing logs of the system and from applications. � Once. True Image Configuration page shows how True Image is configured and the details of backup tasks. MVP guidelines page includes links to useful resources, such.